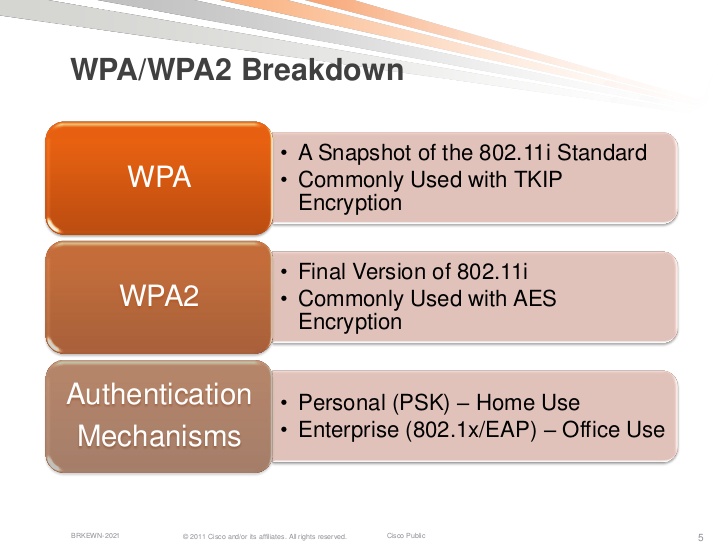
Wep Is A Stronger Form Of Security Than Wpa
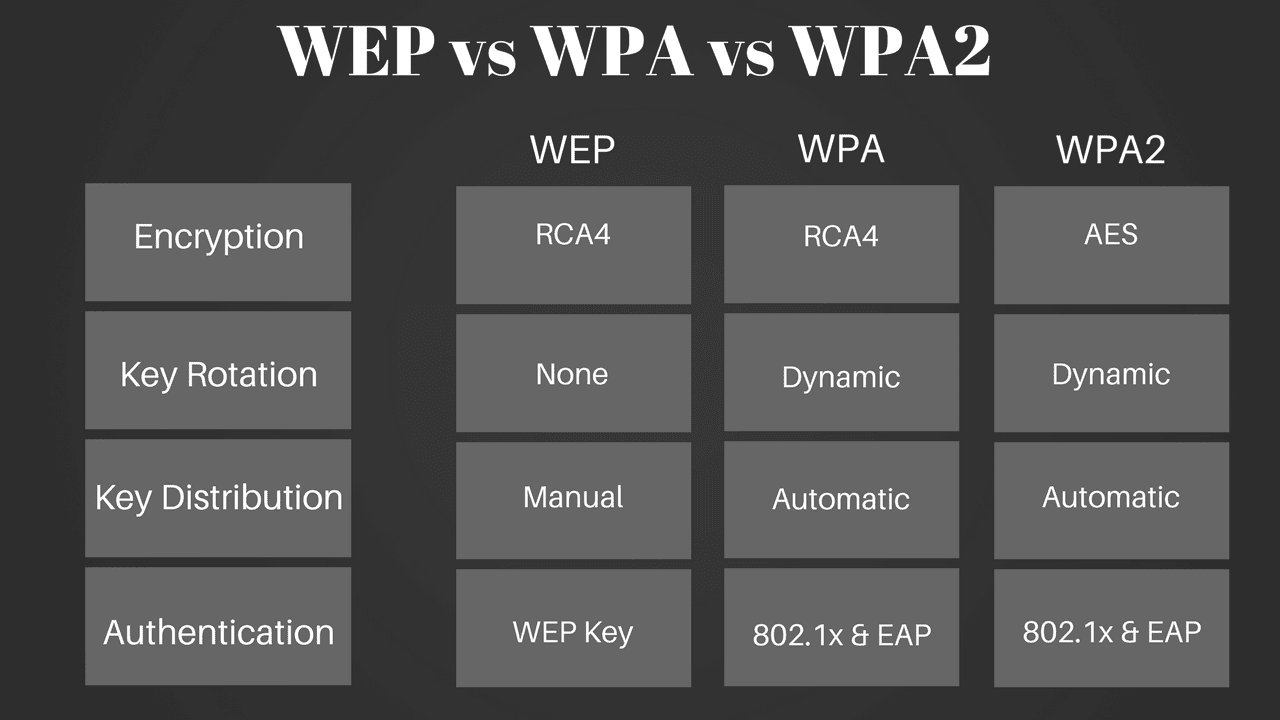
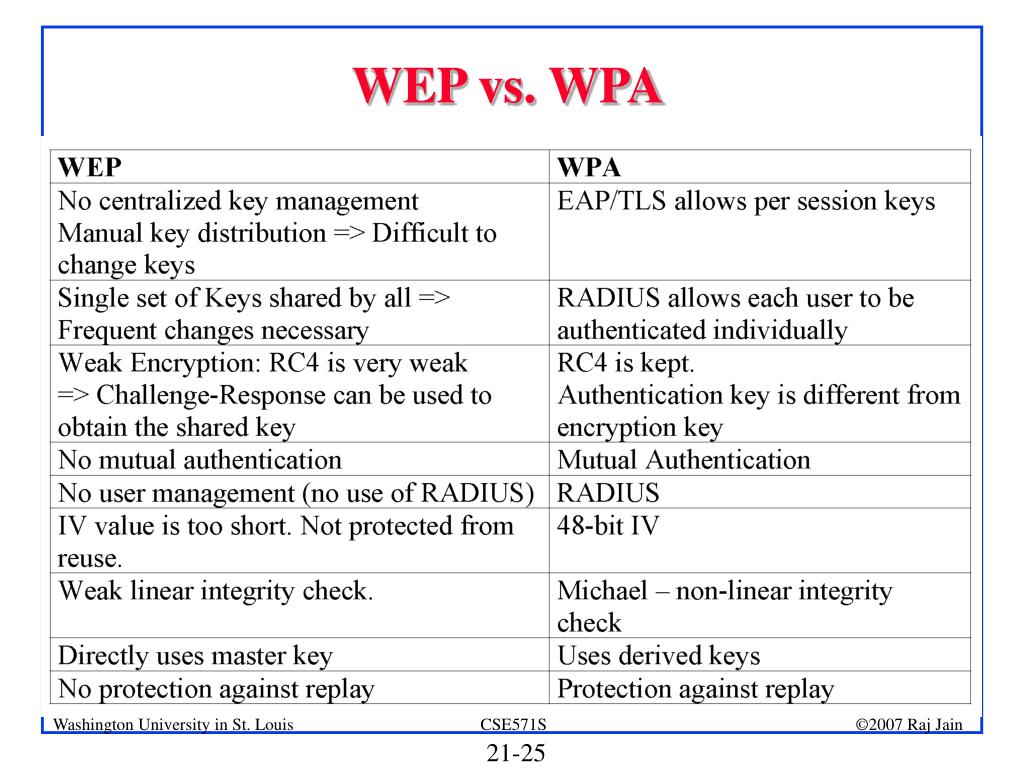
Wep Is A Stronger Form Of Security Than Wpa - Wpa + tkip/aes (tkip is there as a fallback method) wpa + tkip ; Wep ________ is a much stronger protocol than wep for wireless security. P2p networks are most commonly used in home networks. Web while wep provides each authorized system with the same key, wpa uses the temporal key integrity protocol (tkip), which dynamically changes the key that systems use. Web using wep, all traffic is encrypted as a single key, meaning that it uses a static key. 2 which transmission medium transmits data fastest? Wep, wpa, wpa2 and wpa3: This encryption protocol is not secure as a static key is used for encryption. Web wep is a stronger form of security than wpa. Table of contents [ hide] 1 is wep is a stronger form of security than wpa? The protocol named temporal key integrity is incorporated by wpa, which. Aes is substantially stronger than rc4 (as rc4 has been cracked. When choosing from among wep, wpa, wpa2. Web while wep provides each authorized system with the same key, wpa uses the temporal key integrity protocol (tkip), which dynamically changes the key that systems use. Everything else on the. Terms in this set (102) wep is a stronger form of security than wpa. Web while wep provides each authorized system with the same key, wpa uses the temporal key integrity protocol (tkip), which dynamically changes the key that systems use. When choosing from among wep, wpa, wpa2. Sharing files is a benefit of a network. A computer ________ is. Wep ________ is a much stronger protocol than wep for wireless security. Web while wep provides each authorized system with the same key, wpa uses the temporal key integrity protocol (tkip), which dynamically changes the key that systems use. A ________ is a device. Web using wep, all traffic is encrypted as a single key, meaning that it uses a. Aes is substantially stronger than rc4 (as rc4 has been cracked. Web while wep provides each authorized system with the same key, wpa uses the temporal key integrity protocol (tkip), which dynamically changes the key that systems use. This encryption protocol is not secure as a static key is used for encryption. Everything else on the list is a less. Web wep is a stronger form of security than wpa. Everything else on the list is a less than ideal step down from that. Aes is substantially stronger than rc4 (as rc4 has been cracked. It is also known as wired equivalent privacy. Which of the following does not determine processor power? It is also known as wired equivalent privacy. When choosing from among wep, wpa, wpa2. Sharing files is a benefit of a network. A computer ________ is two or more computers connected using software and hardware so that they. The protocol named temporal key integrity is incorporated by wpa, which. Wep ________ is a much stronger protocol than wep for wireless security. Web wep is a stronger form of security than wpa. Web wep is a stronger form of security than wpa. 2 which transmission medium transmits data fastest? This encryption protocol is not secure as a static key is used for encryption. Web central computer provides information and resources to other computers. Wep, wpa, wpa2 and wpa3: This encryption protocol is not secure as a static key is used for encryption. Everything else on the list is a less than ideal step down from that. Web wep is a stronger form of security than wpa. Table of contents [ hide] 1 is wep is a stronger form of security than wpa? This encryption protocol is not secure as a static key is used for encryption. A computer ________ is two or more computers connected using software and hardware so that they. Which of the following does not determine processor power? A ________ is a device. Web while wep provides each authorized system with the same key, wpa uses the temporal key integrity protocol (tkip), which dynamically changes the key that systems use. Table of contents [ hide] 1 is wep is a stronger form of security than wpa? Wep ________ is a much stronger protocol than wep for wireless security. 2 which transmission medium transmits. A computer ________ is two or more computers connected using software and hardware so that they. The protocol named temporal key integrity is incorporated by wpa, which. Which of the following does not determine processor power? Everything else on the list is a less than ideal step down from that. This encryption protocol is not secure as a static key is used for encryption. Wep, wpa, wpa2 and wpa3: Terms in this set (102) wep is a stronger form of security than wpa. Table of contents [ hide] 1 is wep is a stronger form of security than wpa? A ________ is a device. Wep ________ is a much stronger protocol than wep for wireless security. 2 which transmission medium transmits data fastest? Web using wep, all traffic is encrypted as a single key, meaning that it uses a static key. When choosing from among wep, wpa, wpa2. Web central computer provides information and resources to other computers. Web while wep provides each authorized system with the same key, wpa uses the temporal key integrity protocol (tkip), which dynamically changes the key that systems use. P2p networks are most commonly used in home networks. Wpa + tkip/aes (tkip is there as a fallback method) wpa + tkip ; Aes is substantially stronger than rc4 (as rc4 has been cracked. It is also known as wired equivalent privacy. Sharing files is a benefit of a network.WiFi Security Types WEP, WPA, WPA 2 & WPA 3 WiFi Security Types
What’s WPA3 (and the Difference Between WPA3 and WPA2)
WiFi Security Types? How To Secure Your WiFi Network? WEP, WPA, WPA2
WLAN Security WEP/ WPA/ WPA2/ WPA3 YouTube
PPT Wireless LAN Security II WEP Attacks, WPA and WPA2 PowerPoint
Wep vs Wpa and Wpa2 security, difference Explained!
What Is WiFi Protected Access (WPA)?
WEP vs. WPA vs. WPA2 vs. WPA3 WiFi Security Types Explained
Difference Between Wpa And Wpa2 In Wireless Security Configuration
PPT Wireless Security Using WEP, WPA, and WPA2 PowerPoint
Related Post:



:max_bytes(150000):strip_icc()/WPA-2-vs-WPA-1065c13b32d34a95ac1bb133d35c6767.jpg)